Email’s wonderful. It’s a tremendous personal enabler and a genuinely colossal business tool. However, email’s rife with imposters, phantoms, and general ill-wishers. The medium is a hotbed of fraud and deception, with phishing and other less-than-exemplary activities commonplace.
Filters doing their level best to protect an inbox will sometimes find it tricky to sort out the worthy wheat from the cheating chaff. This means that an email you’ve lovingly crafted will occasionally be in the spam folder. Annoying.
How can you ensure your email has the credentials to land in the inbox properly? Happily, there are several techniques to polish up a profile. Grab a chamois and read on.
Email Authentication - What is it?
There are plenty of ways to improve your business’s email deliverability. Getting your authentication right is one of them.
We’ll start by assessing what it is that toils away to keep inboxes safe from scams and free from phishing. Put simply, email authentication is a set of techniques that internet service providers use to decide whether an email is legitimate, in which case it gets waved through into the inbox, or a bit suspect, in which case it’s invited to make its home in the spam folder.
It requires a degree of cooperation between the server doing the sending and the server doing the receiving. They need to speak the same language for the whole thing to function correctly.
How an ISP carries out the authentication is like this. Firstly, it will check that the identity in the “From” field matches the provenance of the email. Secondly, it checks to see if the message appears to have been subject to any change in transit.
On top of these, the ISP will apply a set of rules to screen the email. Where does it get these rules from? You. You decide exactly how stringent you want the protection to be. You then configure your servers accordingly, so you have a degree of confidence that what ends up being let into your inbox is what you want to read and not some nasty surprise.
So Why’s it Important?
Email marketing is hugely popular. It’s cheap and highly effective. The best marketing is multi-channel, so email and phone together are a force to be reckoned with. This is one of the reasons why hosted VoIP provider companies are doing so well right now. But in terms of sheer ROI, email is very difficult to beat either on its own or as part of a broader strategy.
One of the problems with email is that it’s a very hospitable environment for wrongdoers. Phishing, in particular, is ridiculously widespread. If you think not, that’ll be because you’re benefiting from the powers of a working filter.
To give yourself a little taste of what could be, were it not for authentication systems, pop your head into your spam folder from time to time. You’ll likely find yourself sinking in a swamp of swindling, a marsh of money-grabbing, a quagmire of - well, any way you get the idea. Suffice it to say, it ain’t pretty.
In 2021, 47.1% of all emails sent worldwide were phishing emails. It’s a veritable epidemic of embezzlement and is only getting worse.
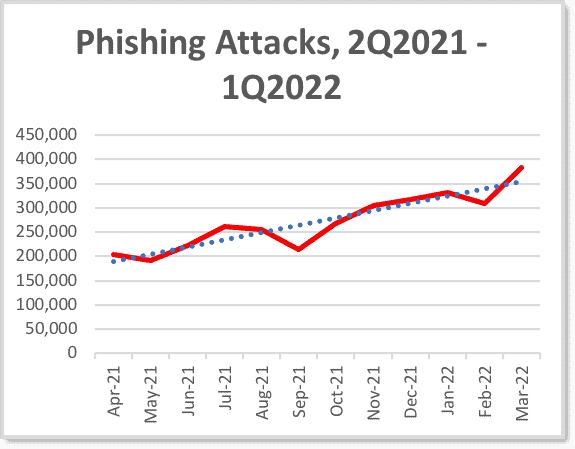
Image sourced from apwg.org
Of course, it does not just attempt to get money out of people that crop up. It can endeavor to get a hapless recipient to open up malware. Or it can be plain, straightforward, annoying, but harmless spam that just gets in the way.
Authentication is essential as far as outgoing comms to customers are concerned too. With the use of logo replication and by meddling with the “From” field, spammers and phishers can send malicious emails to customers that appear to come from your business. The damage this does in terms of trust is enormous.
By ensuring that any outgoing emails benefit from attention to authenticity credentials, you can be confident of lower non-delivery rates, which means more ROI.
Right, so we’ve covered why authentication is essential. Let’s look at some methods of implementing it.
Before we do, it should be remembered that authentication is only part of improving deliverability. It can also be the case that your company’s domain just doesn’t swing it as far as reputation’s concerned. Don’t worry, though - there are techniques you can use to warm up your domain and encourage receiving servers to welcome their emails with wide open arms.
Meanwhile, back to authentication.
Sender Policy Framework (SPF)
_4q7QyAoRE.png?updatedAt=1693702502606)
Image sourced from dmarcian.com
SPF is a technique that focuses on verifying the sender's identity. When a message comes into a receiving server, the ID will be checked to ensure that the originating IP address is on the list of legitimate addresses for that domain.
The SPF record is added in plain text to the server’s Domain Name System (DNS). The DNS is a public record, valid for all to see (but only of interest to those involved in the email exchange).
This has been a viral technique, not least because it’s simpler to configure than a lot of the others. However, some businesses may prefer a more robust means of authentication. Other such systems are available, but, broadly speaking, they are built upon SPF. In other words, SPF is a vital first step to enhanced security.
There are a few concerns that should be highlighted here:
- There can be syntax errors when entering the SPF records, which may lead to a breakdown in the authentication.
- There can be trouble where IP addresses are shared, via cloud applications, for example, which can have consequences for authentication based on IP.
- It can be possible for hackers to circumvent the system by seeming to present perfectly valid domain and email address criteria but to sneak in their email as the return path.
- SPF does not support forwarding. A forwarded email will usually be rejected because it’s the domain of the forwarder, not the originator, that is checked, then turned down due to the mismatch.
DomainKeys Identified Mail (DKIM)
_qPgz81tAz.png?updatedAt=1693702502524)
Image sourced from demarcian.com
The big difference between DKIM and SPF is encryption. The sender starts by deciding which parts of the email should be used for verification. It might be the entire message or just specific components. The area picked gets encrypted.
Upon arriving at the receiving server, the encrypted area is decoded and checked to see if any manipulation occurred en route.
It does this through the use of keys. A public key exists on the sender’s BNS, and a private one inhabits the sender’s email server. An outgoing message ‘hash’ is generated and encrypted according to this private key.
When the message is received, the DKIM signature is assessed, and the DNS is looked up to get the public key. The public key should be able to decode the encrypted hash, or there’s a problem, and the mail will be rejected.
An essential factor to grasp here is that the signature isn’t usually visible to the person receiving the email. The signature is intended for the receiving server’s use, and doesn’t need to be part of the content of the email that’s visible to the intended recipient. This means it doesn’t get in the way, affecting the quality and readability of the message.
Possible drawbacks are as follows:
- It can be feasible for phishers to exploit the possibility that a valid signature might have a different domain than the one in the From field.
- If a hacker signs messages from another user’s domain, they might be able to get authentication by using that domain’s private key.
- Keys can get lengthy and convoluted and can be unwieldy when copying and pasting into the DNS. This can lead to errors.
DKIM’s reasonably practical but is much better when viewed as a partner system used in tandem with the next element on our list.
Domain Message Authentication Reporting and Conformance (DMARC)
This is one of those techniques that makes you want to bless whoever thought up acronyms. In any case, DMARC’s significant contribution to the world of authentication resides in how it tells the server what to do when SPF and DKIM reject messages. This might be quarantining, rejecting, or doing nothing at all.
DMARC also works by enforcing the use of the domain set in the “From'' field, preventing hackers from misappropriating the appearance of a trusted domain.
Finally, DMARC provides excellent reporting functionality, so you can request accounts of what’s been happening with failed sendings and attacks on your domain. These will enable you to stay on top of any attempts by hackers to send out mail as if from your company.
These three are the most common ways to authenticate emails that are in current use. Here’s a handy pictorial to help you remember the differences between them.
_c7HQ2XC-x.png?updatedAt=1693702502282)
We’ll now turn to a fourth technique, which is very different and much easier to get your head around.
Brand Indicators for Message Identification (BIMI)
BIMI’s not been around long, but it is hoped to significantly increase email deliverability.
Its premise is nice and simple to understand. Next to the sender’s name in the “From” field is a miniature graphic. This is usually something to do with the originating company. Often a version of the logo could be a picture of something related to the core business.
For example, if it’s a waiver agreement template from Pandadoc, it might be a panda if it’s an update from an outdoorsy business, perhaps a tent. If it’s a shoe flash from a shoe shop, maybe a shoe. And so on.
The recipient then sees the graphic next to the sender’s name, which, on a very cosmetic level, gives the feeling of authenticity.
Here’s the significant bit, though. BIMI’s not available to just anyone. To use the graphic, the sender has to accommodate and observe specific authentication protocols.
BIMI’s a simple but very effective way of assuring recipients that the message is from a legitimate source. As it becomes more widely used, people will become accustomed to looking for the graphic and treat its omission as a reason to be suspicious about the email's nature, contents, and origin.
_mVTWdxnkM.png?updatedAt=1693702502597w)
Image sourced from dmarcly.com
It also means that the recipient is less likely to incorrectly surmise that an email is a spam, which means higher delivery rates.
The Others
Several other techniques are worth running through here. They’re less widely used or a bit long in the tooth, but you should be aware of them just in case they pop up in your next authentication chit-chat.
Sender ID
This was developed by Microsoft and is somewhat similar to SPF. It works similarly in looking for mismatched data that flags up a problem with the sender's authenticity. Sender ID will then attach one of several codes to the message, running from Pass (in other words, this one’s OK) to Perm Error (this one has a significant irregularity in its DNS).
It was developed for use with Hotmail and Windows Live Mail, both of which have now gone to the big cloud in the sky (ie, not merely cloud-based, but kaput), so Sender ID isn’t often encountered now. However, it is used in specific applications, such as some Microsoft servers.
Author Domain Signing Practices (ADSP)
This is an extension of DKIM, in which domains publish the signature information of senders.
Vouch By Reference (VBR)
This is a method of authentication that uses certification provided by third parties.
DNS-based White List (DNSWL)
Domains to be trusted are included on a list that a recipient can use to establish the sender's authenticity.
Bulk Validation
If you’re about to send out a marketing campaign and you want to be sure that the emails you have are legitimate, it’s worth considering a bulk validation. Lists of email addresses are uploaded to the validating organization in TXT or CSV format, and they are then processed to check for any wrong data.
The cleaned-up list is then returned to the client, who can be confident of much better deliverability and engagement rates.
How to Set up Authentication?
It’s not that tricky to set up these facilities. Let’s take one popular email platform to see what’s involved. Hubspot is a widely used CRM that has a robust set of email marketing tools. If you want to use DKIM when sending out emails from Hubspot, here’s how.
_lxj4zAO5X.png?updatedAt=1693702502539)
Image sourced from knowledge.hubspot.com
Start by authenticating your domain within your Hubspot account. Create your DKIM signature and connect it to your DNS records. Hubspot will generate data for you to input into your DNS record, which will authenticate your outgoing emails. That’s pretty much it. Other email platforms will be broadly similar.
When to Look at Your Authentication?
Most of the time, your authentication system will run nice and quiet in the background, busily doing your business with unparalleled amounts of sound. However, you should check it periodically to make sure everything’s still functioning as it should. After all, what might have sufficed in the past can be rendered obsolete by the passage of time and the development of malicious practices.
There are several ways of doing this. The most basic approach is to adopt manual testing concepts like just sending an email to your account and seeing what happens. You’ll then see exactly what transpires in terms of the message being safely delivered in the first place and not shoved into Spam. A side benefit here is that you can pretend to be the customer. In doing so, you can try to appreciate how the email comes across to someone not connected with the company. Is it clear? Is it too pushy? Is it too passive?
Another technique worth adopting is monitoring your marketing data. If there are unexplained surges in rejected messages or a plummeting engagement, then your authentication might be something amiss. Your email platform should be able to deliver this information - go to the marketing area and check email details to see the performance data you need.
DMARC is another source of information, so do use it if you’ve got it. It’s a good idea to do this kind of check regularly in any case, but especially before any significant marketing operation.
After all, marketing campaigns aren’t cheap, and you don’t want your effort scuppered because of faulty authentication. Authentication will ensure that this connection gets made in the first place. Another good idea is to check your authentication records if you’ve changed your DNS provider, as this can play havoc with authentication.
Conclusion
We can learn a lot from newspapers and other media. They spend a great deal of time and effort establishing and nurturing their reputations so that people learn to trust them. Anything that might interfere with that reputation - an uncorroborated story, for instance - is treated with extreme caution.
So it should be with anything that impacts your business profile. Being associated with unwanted elements cannot harm your hard-won reputation for honesty and competence. Using email authentication, you can be sure that this crucial part of your communication with your customers is as free as possible from sham, scam, and spam.






