How often do you interact with your email box? I bet pretty often. Whether you receive a critical business email, write a business partner, or start an outreach campaign to target leads, the email system becomes crucial for your operation.
Unless you need to do email marketing or set up a corporate email box, the email rules and concepts are unlikely to come to your attention. Yet, knowing how email protocols work, how to secure email port systems, and the difference between POP and IMAP protocols can give you a specific advantage.
Read on to learn more about the types of email protocol configuration and email server settings. Such information will likely help you improve your email marketing and optimize the working process.
What Protocol Does Email Use?
The system utilizes different email protocol configurations, particularly SMTP, POP3, and IMAP. They primarily differ by function.
Let's say you, a sender with the following email address [email protected], decide to write to a prospect whose name is Alex and whose email address is [email protected]. What is the email path from your inbox to Alex's?
The whole email journey concerns the concepts of email clients, servers, protocols, and secure email ports that work on various levels. Specific protocols act as the instrument to submit the messages, some to relay and others to receive them.
What Mail Protocol is Used to Send Mail Messages to a Server?
The protocol used to send an email over the internet is the Simple Mail Transfer (SMTP) protocol. It defines how the email gets from the sender's email server to the recipient's email server.
In this regard, it is vital to understand how email goes from one server to another under the IMAP, POP3, and SMTP protocols.
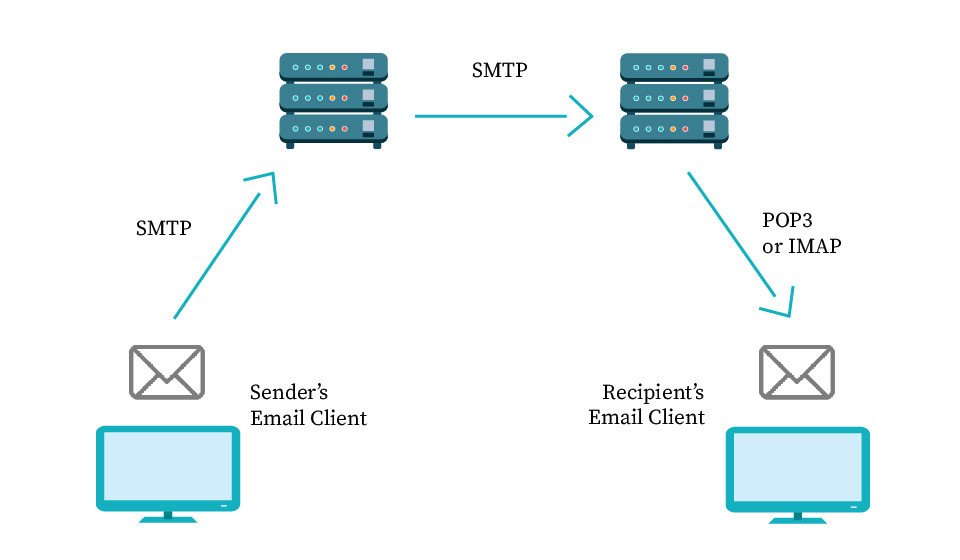
First, you give the signal to the SMTP server as a sender. The particular server is an application regulated by the above protocol that processes data and sends it to other servers.
After it, the SMTP of your email client connects with the SMTP server of the recipient and authenticates their email address. In our case, the target SMTP server is randomemail.com, while its specific name is likely smtp.randomserver.com. It stores your email message and checks the validity of the recipient's email address.
In the next stage, the other two types of email protocol configuration come into play. When the recipient's or Alex's server gets an email, it contacts POP3 or IMAP servers and transmits the message to them, from where the receiver's email client accesses the message.
Notably, the email protocol uses a specific secure email port or SMTP protocol port number, so picking the correct number can even help you with email deliverability.
After the deliverability audit, some people find that they use the wrong ports or protocols, which experts consider spam highways. In these cases, even if you use an email finder add-on to discover the email addresses of leads, it will be hard for you to go through the email filters of providers.
POP3 vs. SMTP vs. IMAP
SMTP: As you may guess, compared to POP3 and IMAP protocols, the SMTP email protocol has a different function. It links your client with the email server's provider, identifies the email server to which you send the message, and transfers the email there. That way, the SMTP allows the forwarding and transmitting information from one server to another.
POP3 and IMAP are email protocols that have incoming or receiving functions. What does it mean? Their main goal is to receive messages. In this regard, one may consider them a bridge between the mail server and the receiver's email client. With them, a corporate actor, entrepreneur, or employee can get the email from the server.
What is POP3 used for?
The POP3 is the email protocol that ensures retrieving or transferring the upcoming emails from the mail server to the receiver's mail client. The main algorithm behind this email protocol is that it is concerned with connecting to the server, downloading the email messages, deleting the copies from the server, and disconnecting from it.
Notably, the fact that the copies of the messages are deleted before the disconnection, even though you can opt to save them by modifying the default settings, makes POP3 different from the IMAP.
Also, it is known for solid authentication instruments used to establish greater privacy for the user.
How do people utilize IMAP?
The IMAP protocol is another protocol used for the receiving of messages. Its distinctive feature is that you can access your email box from different devices. Such an event is possible due to the idea that the server does not eliminate emails after their delivery to the email client. That way, the IMAP email server becomes the storage of the files while the user can access it with the email client if there is an Internet connection. The downloading of the message starts when the recipient decides to open a specific email.
As a result, you can see that SMTP has a sending function, while IMAP and POP allow people to receive emails.
However, on the technical level, the SMTP, IMAP, and POP have different configurations that produce these functions.
For instance, the significant distinction of SMTP protocol from the other two refers to their email port configuration.
What is a secure email port? Before all, a port allows communication between the servers, connecting one server to the more extensive network. In particular, the port appears to be an identifier of what service or application is running on the server. By setting the secure email port, the sender can convey its message to the correct server.
Picking the SMTP protocol port number can determine whether your message will be encrypted or not, relayed or submitted. Here are the number of ports that are used by the SMTP protocols:
- 25 Is a widely used port for relaying information under SMTP protocols. The main issue is that it is old and widespread, being the main channel for spammers to send junk emails. That's why certain providers can block it.
- 465 is the port that many consider a substitute for the port mentioned above. The main feature is that it offers encryption (via SSL technology), adding to the security of the email's content. Yet, it has been replaced by better technologies in the port discussed below.
- 587 is the port using advanced security protocol, contributing to better protection against malware and spam. Today, many companies use it as a preselected option due to the STARTTLS command protocol, allowing ciphering of the connection with the TLS/SSL.
- 2525 is another option, yet not as recognized as the previous one. It also encrypts data; however, the area of its utilization is usually concerned with cloud hosting services. Thus, you should apply it if you find out that data transfer using the previous ports leads to failure.
Notably, the POP3 and IMAP use different ports, which will be covered in another section.
In the end, the SMTP ports define how one SMTP server would send the message further to others. If you use the wrong configuration, it can result in bad consequences for your campaign.
Even if you have all your leads organized with some software and have the correct email address, selecting the wrong ports configuration for submitting and transmitting data can give you some trouble. The most acceptable option is port 587, as it is a recognized and widely-used solution for SMTP servers.
POP3 vs. IMAP: The Difference Between Receiving Protocols
You already know that POP3 and IMAP have a similar function allowing receiving emails. Nevertheless, they have distinctions that can give an email system certain benefits regarding usage, storage, organization, access, and other things. They come from the idea that one stores the email on the server while another downloads it to the computer.
Server Storage
First, if a person gets many messages, they will likely choose the POP3 protocol. Why? The IMAP email servers store the email messages on the server and leave copies of the messages affecting the storage space of the email server.
At the same time, the POP3 contemplates downloading the messages from the POP3 incoming mail server to the computer and deleting the copies. As a result, picking the POP3 seems to be a more favorable option as the IMAP server storage may have limited capacity; unless you want to save space on your computer. However, considering the weight of the messages, they should not be crucial to your operation.
Regarding deliverability, you can suggest that the significant business actors likely have POP3 email servers due to the number of incoming messages. Therefore, you should consider the specifics of the POP3 protocol to create outreach campaigns targeted at them.
Access and data manipulations
Importantly, access to the files plays a crucial role as well. If you have a good Internet connection, then IMAP can be a better choice in terms of access. Why? The IMAP email server stores the message copies on the server. It means you can access them anywhere, irrespective of the client or device you possess.
The same applies to the retrieval of messages. For instance, if you use the Gmail email system, you will utilize the IMAP system. If you have an app installed on your phone, you will get a notification on the incoming messages both on the computer and the app. In this regard, the IMAP email servers seem to be more functional.
Simultaneously, the IMAP email server offers excellent synchronization and organization opportunities. The explanation is that it focuses on storing the messages on the server. Thus, the latest IMAP versions allow a person to synchronize actions performed with the email on different devices.
For instance, if you read certain emails or decide to move them in the trash by using your phone, you will not need to repeat this action when utilizing the PC. This action will be synchronized automatically. Besides, this type provides greater organization by hierarchically sorting the messages into folders.
However, there is a condition when the incoming POP3 server can be a better option. For instance, when you have a bad Internet connection and still need to access your messages all the time, POP3 will allow you to access, read and work with the old or received emails without the Internet connection.
Computational load effect
The installation of each system requires specific resources from the computer. In this regard, the POP3 email server requires less CPU and memory of the computer for the operation and running of the necessary actions. Compared to the IMAP, which allows synchronization and better organization, the user will need more computational capacity to perform actions between the server and the client.
If you don't have enough resources, POP3 will be the best option. Yet, you will sacrifice the functionality and better access to the emails.
Quickness of operation
One can ask which of the types of email protocol configuration is quicker. Well, the answer to this question is not definite. In most cases, when downloading new emails, using the IMAP server would be faster, as it downloads the parts of the email, like headers for the display.
Then, only if you choose to proceed with the specific email will it start downloading the rest of it. Simultaneously, when a person utilizes the POP3, then a user downloads all of the new emails at once.
Ports used
Besides, considering the different mechanics at the center of the protocols' operation, they use various ports. For instance, the POP3 protocols would use port 110 to establish the connection with the SMTP server, while the IMAP would utilize port 143.
Interestingly, they as well have distinctive ports in case of message encryption. If the messages are encrypted under SSL/TLS layers, the IMAP will resort to alternative port 993, while the POP3 port 995, respectively.
As a result, both of these secure email protocols can be beneficial. The decision to apply one of them should derive from the user's preferences. Yet, remember that prominent corporate actors usually have their own servers working on POP3 due to its higher security.
Which Protocol is a More Secure Alternative to Using SMTP for Outgoing Email?
Some may believe that hackers can get to it if the message is in transit from one server to another. It is true; that's why people have tried to find a more secure protocol option. However, there is no other secure alternative. Instead, one can use Transport Layer Security (TLS). A layer of protection contributes to the SMTP protocol and encodes the message.
The main principles that protect data transmission refer to the TLS handshake and TLS record layer concepts. The first one contemplates the process in which two servers exchange messages and authenticate, verify one another and create keys for further exchange of information.
The second is concerned with transporting the data or messages securely with the help of the keys. The records, managed by the compressions and decryption algorithms, contain information about the message, referring to the content, protocols, length, and message authentication codes.
The TLS protocols have been developed, and the experts today recognize different types of them, particularly Opportunistic TLS, Forced TLS, and STARTTLS.
Moreover, another method to encrypt the message is to apply Secure/Multipurpose Internet Mail Extensions (S/MIME). The basis of their operation lies in applying key cryptography or digital signatures. It is a way to improve security, yet, some may find weak spots referring to metadata.
In the end, they are only the ways to improve the SMTP protocols as the latter remains the back-end solution for relaying data and, thus, messages.
Final Words
This article shows that the email system has several protocols that help users transmit and receive messages. In particular, the SMTP email protocols ensure that the data is submitted and sent from one server to another. Simultaneously, the POP3 and IMAP email protocols are responsible for receiving the information, accessing the SMTP server, and getting the message to the receiver's email client.
For sure, they have various principles behind their work. The POP3 allows downloading the messages, while the IMAP depends on the Internet connection to access email and stores copies on the server. Besides, all types of email protocol configurations have distinct secure email ports that affect the transmission of the data and its security. To improve the safety of the email transmission, you can use email ports applying TLS technology that works on top of SMTP protocols encrypting the messages.



![Best Data Enrichment Services [2025]](https://ik.imagekit.io/debounce/wp-content/uploads/2021/04/popular-data-enrichment-tools-300x139.png)