As more and more of us choose to run important parts of our personal and professional lives on the go, staying connected digitally is becoming almost a necessity for our everyday life. Whether it’s about buying a new pair of shoes using our mobile phone or checking our work email while we are out and about, the opportunities that the digital world keeps offering us are virtually boundless.
Nonetheless, this can also bring about fresh challenges that we must be aware of. The main one is, without any doubt, security. On the one hand, we have an increasing number of people accessing confidential information – such as email messages – from digital devices, while on the other, we witness a surge in cybercriminals ready to exploit those potentially vulnerable situations to steal data, money, and identities.
And while this scenario may sound catastrophic and should be cause for concern, it’s also true that you can take actions to bulletproof the information that your personal and professional email accounts store. The answer lies in multi-factor authentication (MFA). There are a number of Mail Chimp alternatives that offer MFA for email.
Understanding Basic Authentication
Instead of jumping straight into the topic of MFA, we thought it would be necessary to clarify what authentication is, why it is important, and how it works. When we talk about authentication, all we mean is simply the process of checking that you are really who you say you are.
This is essential, especially if you have to access confidential data – such as that contained in an email database, for example – or to sign into your email account on a specific website. To ensure that only the right individual has access to the correct type of systems and information, it is necessary to prove that they are the legitimate owner of that account.
With standard authentication, you can simply enter the username and password you created when you first opened that account. Sounds easy enough, right? It is why traditional authentication methods are much more prone to failing and causing security issues.
All it takes for someone else to access your account is to know what your email is – a relatively straightforward thing to find out – and guess what your password might be. Experienced hackers can crack even the most (seemingly) complex passwords, which grants them access to areas that they should definitely not be in.
Because this type of authentication is so ineffective, more and more online users are opting for a much stronger and more reliable method: multi-factor authentication (MFA).
What Is Multi-Factor Authentication (MFA)?
Simply put, multi-factor authentication (often also known as two-factor authentication) adds one extra layer to your cybersecurity. This strategy requires you to prove your identity in at least two ways, including providing passwords, answering specific questions, and more.
Why Is MFA So Crucial? The Main Benefits to Consider
There are plenty of benefits that both individuals and corporations can achieve through MFA. Below we will examine some of the most significant ones.
It Improves Password Health
If you purely rely on passwords to protect your most confidential and essential email accounts, you are making a big mistake that might cost you a lot. This is because passwords are often shared, re-used, and can even be guessed by cyber criminals.
While not eliminating passwords, an MFA approach to your cybersecurity means that their health and effectiveness are much higher and more safeguarded than they would be by using passwords alone.
It Boosts Overall Security
Enhanced security is one of the most crucial advantages of MFA. Hackers might be able to break into a personal email account by cracking a password. Still, if they also need to provide further information or proof of identity, the game will inevitably get trickier for them.
It Works with Single Sign-On (SSO)
If MFA sounds like a complex and time-consuming task, you’ll be pleased to hear this: MFA can be incorporated into specific apps and integrated with single sign-on. This means that users won’t need to keep creating lots of different passwords for all the apps they use or for their different email accounts while at the same time enjoying a much stronger level of security.
It Helps Ensure Regulatory Compliance
Certain industries, such as financial services, healthcare, and insurance, to name but a few, are heavily regulated when it comes to data privacy and security. This makes MFA an absolute no-brainer, as it helps to make sure that only authorized users have access to specific data and systems.
It Is Easily Scalable
If your company is undergoing a big growth process, then you will be happy to learn that MFA can be a fantastic way to strengthen your entire systems and networks while simultaneously helping you save time and money. By combining MFA with SSO, for example, you will remove the need to create multiple passwords, which in turn speeds up the email login process, enhances the user experience, and takes some pressure off your IT department.
It Can Adapt to Different User Cases
Did you know that data such as IP address and geolocation can be used in adaptive MFA? This is because such situations often demand enhanced security, and that’s exactly what MFA offers you. Think about it as a way to recognize legitimate emails from spam emails, and help you take action accordingly.
It Strengthens the Security of Mobile Devices
More and more people have started accessing and using their professional email accounts on the go. This means that mobile devices are no longer simply used for personal purposes but have become real tools for productivity and profitability. For this reason, ensuring that our mobile devices are always fully protected is paramount.
This is something that MFA lets you do, exceptionally if you choose to integrate it with SSO. By doing so, you will be able to access any email you need, from anywhere, and at any time, with the peace of mind that only you have access to that information.
It Is Very Customizable
Another great, yet often underestimated, reason you should choose MFA is that it allows for a great degree of personalization. Whether you prefer biometric identification or answering personal questions, with MFA, you will be able to deliver an extremely smooth and customized user experience.
MFA: What Are Its Main Challenges?
We would be lying if we claimed that MFA is a perfect science. If you decide to adopt MFA, you must be aware of some potential challenges you might face – below are some of the top ones, together with some great tips on overcoming them.
Difficulty in Boosting Adoption Rates
Just like in many other technology-related situations, getting the right buy-in from your email users is not always easy when you suggest implementing MFA. The reason? The majority of people believe that all the added layers of security to get access to something like an email account are unnecessarily cumbersome and time-consuming.
How to Fix This
To get around the perceived complexity of MFAs, you can act on two fronts. On the one hand, you should educate and train your employees on the importance of having a MFA in place (as you might have done with email protocols), while also showing them how quick and easy the whole process actually is. On the other hand, you need to select the right type of MFA method and technology to make user authentication as rapid, simple, and pain-free as possible.

Image sourced from dataprot.net
Automated Phishing Attacks
While MFA drastically reduces the likelihood of a phishing attack being taken out against your business, it unfortunately doesn’t remove it completely. This is especially true of automated phishing attacks which, frustratingly, are a very common occurrence in email-related cybercrime.
How to Fix This
You must keep educating your employees on how to identify potential phishing attempts, as well as how to act quickly whenever one is spotted. Also, remind them to only open safe links on emails, and to report anything odd or suspicious to their line manager straight away.
Delayed Reporting of Security Concerns
Did you know that most security breaches take as long as 200 days to be identified? Imagine how potentially catastrophic this might be, especially for a company operating in a heavily regulated industry. This is why it’s vital that whenever one of your employees spots something suspicious, they take immediate action by flagging it to you.
How to Fix This
Just as you might sign your staff up for a localization QA if you plan on expanding globally, you should also provide training for detecting security concerns. Make sure to train your entire workforce on how to spot the most common signs of a security breach, especially in terms of compromised email accounts. These often include:
- A sudden change in passwords
- The receipt of phishing emails
- The notification of login attempts from unknown IP addresses or locations
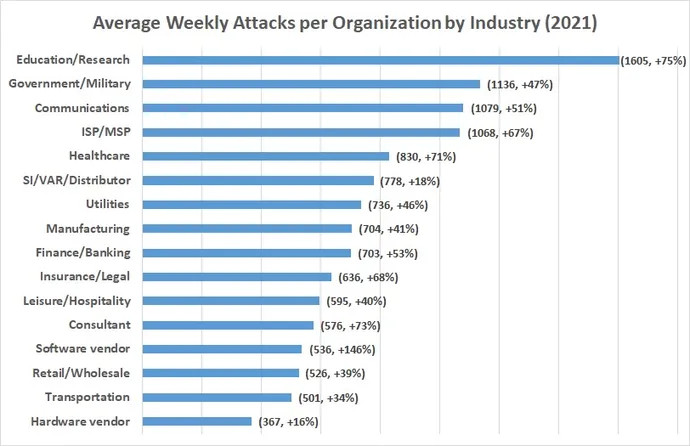
Image sourced from darkreading.com
Types of MFA Methods
Not all MFAs for email were created equal. Below are some of the most popular types of MFA methods currently available. Familiarizing yourself with all of them will allow you to understand which ones are best suited to your unique needs.
Authenticator Apps
Authenticator apps leverage time-based algorithms that check the identity of users to grant them access to a system.
Email Links or Codes
By using this MFA method, a unique link or code is sent to your email address (pay attention to the email subject line to make sure that you do not miss the message).
Fast Identity Online Security Key (FIDO2)
This MFA method works by plugging either a USB drive or NFC device into a system and providing user authentication.
OATH Software Tokens
Configured as either time-based or event-based, these tokens are based on the RFC 4226 HOTP algorithm.
SMS
Sometimes, even a simple text message can work as a very reliable and effective email MFA method. Generally, systems send authentication passwords through text messages, without the need for users to download an app or subscribe to a service.
Smartcards
Smartcards work in the same way as traditional keys, granting people access to specific locations – both online and offline.
Soft Token Software Development Kits (SDKs)
This method relies on cryptographic processes to authenticate a mobile device.
Voice Recognition
With this MFA method, users’ voices are recorded, saved, and used to authenticate users at the time of logging into apps or websites.
How to Implement MFA for Email in Your Company
Let’s now take a look at how, in practice, you can implement MFA for email across your business.
Select Your MFA Solution
First things first: you will need to choose one of the many MFA solutions currently available. If your employees work a lot using mobile devices, then it might be a good idea to opt for a mobile-ready authentication app.
Implement MFA for Your Admin Accounts First
Before you extend your MFA to your entire workforce, it makes sense to start working on your admins’ email accounts first. This is because, generally, it’s these accounts that are more vulnerable to external cyber-attacks, as they tend to contain much more sensitive information.
Adopt a Company-Wide Approach
After ensuring that all your admin accounts have MFA in place, you need to swiftly move on to securing the rest of your workforce’s emails. To make sure that higher data security doesn’t come to the detriment of user experience or productivity, remember to adopt the same MFA solution across your organization.
Consider your chosen MFA tool as some sort of central brain, where all your systems and applications act as nerve endings of a neural network (read here to discover, exactly, what is a neural network).
Keep Communicating and Offering Support
The implementation process might prove complex, and you might encounter some resistance or complaints from your staff. Therefore, it’s crucial that you always keep the communication open, and that you keep asking your employees to provide feedback while encouraging them to seek support if they come across any issues.
Secure Your Older Applications, Too
Most corporations, even the ultra-tech-savvy ones, tend to have a bunch of legacy systems or custom-made applications that do not support your MFA method. If that’s the case for your company, too, don’t simply ignore them: this might put you in a really dangerous position.
Instead, consider upgrading or updating them or, when not possible, phasing them out entirely. And remember: all your new systems and applications from now on will need to be able to support your chosen MFA solution.
Be Prepared to Tackle New Challenges
While you have prepared yourself and your team for this new, and possibly huge, overhaul of your ways of working, you need to maintain an open mind throughout the entire process and beyond, as fresh challenges and difficulties are always around the corner.
For example, some of your employees might still make mistakes that could endanger your system, such as losing an important card or key, or getting themselves locked out of a system when they urgently need access. In these situations, you must remain calm and try to avoid placing the blame on specific individuals, especially when addressing the problem in public.
Consider, instead, organizing further training and, if one of your employees is struggling particularly with email MFA, ask them if they would like to be supported by a team leader or line manager as they get more and more familiar with the new solution.
Ready to Bulletproof Your Systems?
Ensuring that all your personal and professional data is always safe is paramount, especially as more and more people these days perform a wide range of important (and delicate) actions via digital devices.
In this guide, we explored how multi-factor authentication (MFA) for email can help both individuals and corporations to achieve greater data security and protection from external cyber-attacks. While adopting an MFA solution for the first time might feel like a daunting task and might even encounter some resistance from some of your email users, remember that there is so much more at stake here.
Namely, people’s data, money, and identities, which can be included in email lists, financial apps, subscription services, and more. This is why MFA should be a no-brainer for both private and professional users.





![The Ultimate List Of Email Analytics [2025]](https://ik.imagekit.io/debounce/wp-content/uploads/2022/01/email-analytics-you-should-track-300x139.png)
