Imagine sending an important email to a client only for it to end up in their spam folder or not reach them at all. Even more alarming, imagine someone impersonating your domain and sending fraudulent emails in your name, leading to malicious email spoofing and phishing scams.
Such scenarios may seem farfetched to you, but they’re surprisingly common. Check out the stats below:
- Nearly 45.6% of all emails sent worldwide went to recipients’ spam folders.
- 96% of phishing attacks are made through email.
This is why email authentication protocols are important. This detailed guide will dive deeper into the four key email authentication protocols—DKIM, DMARC, SPF, and BIMI—and the validator tools to use. But first:
What Is Email Authentication?
Email authentication is the process of verifying the legitimacy of an email message. It involves using multiple protocols that confirm an email comes from who it claims to be from and that the content has not been altered during transit.
While email authentication is essential for all email senders, it’s especially important for businesses and organizations that rely heavily on email communications. In fact, in 2024, Google and Yahoo require all bulk senders to set up SPF, DKIM, and DMARC email authentication methods for their domains.
How Email Authentication Works
So, how does email authentication work? Here’s a breakdown of the process:
- Sending: The first step is sending the email, which is done from a specific domain or subdomain. The domain is the unique identity that comes after the “@” symbol in an email address. While sending an email, the sender’s server attaches authentication details to the email header. These details are simply the rules that the receiving mail server will use to authenticate the email.
- DNS Lookup: The receiving server performs a DNS (Domain Name System) lookup to retrieve the sender domain's SPF, DKIM, and DMARC records. These records contain the rules and public keys needed to verify the email.
- Delivery Decision: Based on the results of the SPF, DKIM, and DMARC checks, the receiving server makes a final decision, which will fall into the following categories:
- Deliver: If the email passes the SPF, DKIM, and DMARC checks, it is delivered to the recipient’s inbox. Here’s an example of a delivered email that passed all three checks.
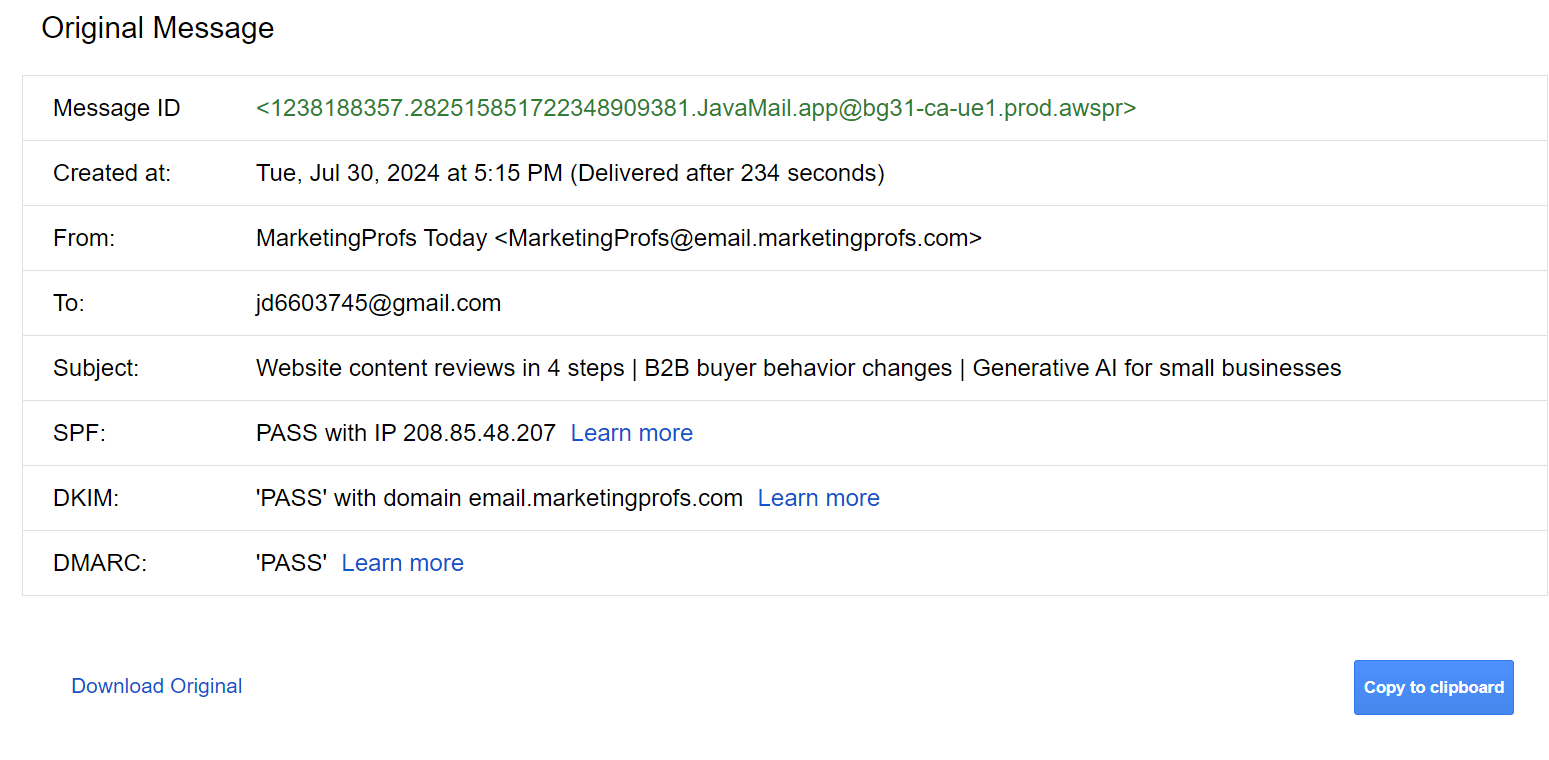
- Quarantine: An email that fails the authentication check but is not considered an immediate threat is quarantined. For instance, it could be placed in the spam email folder, pending the email administrator's review.
- Reject: If the email fails the authentication checks and is deemed suspicious or malicious, it is rejected outright. Malicious emails are bounced back to the sender's addresses or discarded.
You could simply look at the email authentication process as the sending mail server and receiving mail server communicating to ensure the message gets to the recipient untampered.
Important Email Authentication Protocols
Each email authentication protocol addresses a specific aspect of email security. Here’s an in-depth look at these pillars of email authentication:
1. SPF (Sender Policy Framework)
SPF allows domain owners to create a DNS (Domain Name System) record with a list of IP addresses authorized to send emails from that domain.
When an email is sent, the receiving mail server checks the SPF record to verify that the email is coming from an authorized IP address. If the IP address matches, the email is considered authentic.
• Validator Tools:
Some of the tools you can use to validate the components of the SPF record include MXToolbox’s SPF Record Check, PowerDMARC’s SPF Lookup, Google Postmaster Tools, and EasyDMARC SPF Record Checker.
The tools measure the following key parameters to ensure that your SPF record is correctly configured and effective:
- IP Addresses: The record specifies the authorized IP addresses.
- Syntax Errors: Checks for any syntax errors in the SPF record.
- Sender Domain: The domain in the sender’s address is checked against the SPF record to ensure it matches the authorized domain.
Let’s see how a basic SPF record looks:
v=spf1 ip4:192.0.2.0/24 ip4:198.51.100.123 include:_spf.google.com ~all
- v=spf1: Indicates the SPF version.
- ip4:192.0.2.0/24: The authorized IP range (192.0.2.0 to 192.0.2.255).
- ip4:198.51.100.123: The specific authorized IP address (198.51.100.123).
- include:_spf.google.com: This section tells the server what third-party organizations can send emails on behalf of the domain. For instance, our example allows Google's mail servers to send emails for the domain.
- ~all: Specifies a soft fail for emails that don’t match the SPF record. They will be marked as spam but still accepted. The alternative is -all which signifies that unlisted emails should be rejected.
While SPF is great, it has its limitations. For instance, SPF authentication verifies the sender’s domain using the Return-Path, not the “From:” address that recipients see. Therefore, phishers can pass the check by using a fake domain in the Return-Path address and forging the “From” address.
This is why you need other email authentication protocols to fill the gaps.
2. DKIM (DomainKeys Identified Mail)
DKIM verifies that an authorized mail server sent the email and that its content was not altered during transit.
It works by using cryptographic techniques to sign emails. When an email is sent, the sender’s mail server generates a unique digital signature based on the contents of the email and a private key. This signature is added to the email's header.
The recipient's mail server then uses the corresponding public key, published in the sender’s DNS records, to verify the signature. If the signature is valid and matches the public key, the email passes the DKIM check.
• Validator Tools
Several tools can help verify and troubleshoot DKIM configurations. They include DKIMValidator.com, Site24x7 DKIM Validator, SimpleDMARC DKIM Checker, EasyDMARC DKIM Checker, Unspam DKIM Checker, and Dmarcian’s DKIM Inspector.
The key parameters these tools validate include:
- Signature: The digital signature in the email message header is verified against the public key published in the sender's DNS records.
- Domain: The domain in the DKIM signature is checked to ensure it matches the domain in the email's "From:" address.
- Selector: The selector is part of the DKIM signature that specifies which public key to use for verification.
Here’s an example of a DKIM record.
v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCz4EZLtxhU3jY5EJ/GV6xS…
- v=DKIM1: Indicates the version of DKIM being used.
- k=rsa: Specifies the key type, in this case, RSA.
- p=...: The public key used to verify the DKIM signature.
The DKIM email authentication protocol, like SPF, also has its limitations. The main one is if bad actors get your DKIM keys, they can easily use them to impersonate you.
So, ensure you regularly change your keys. If you choose to get your DKIM signature from your email service provider (ESP), avoid those that give their users similar signatures.
Popular email marketing tools like Mailchimp, GetResponse, or MailerLite make it easy to authenticate domains owned by you or your organization with DKIM. The tools come with different feature sets and price tags, so you’ll want to sign up for their free trial accounts and test them thoroughly.
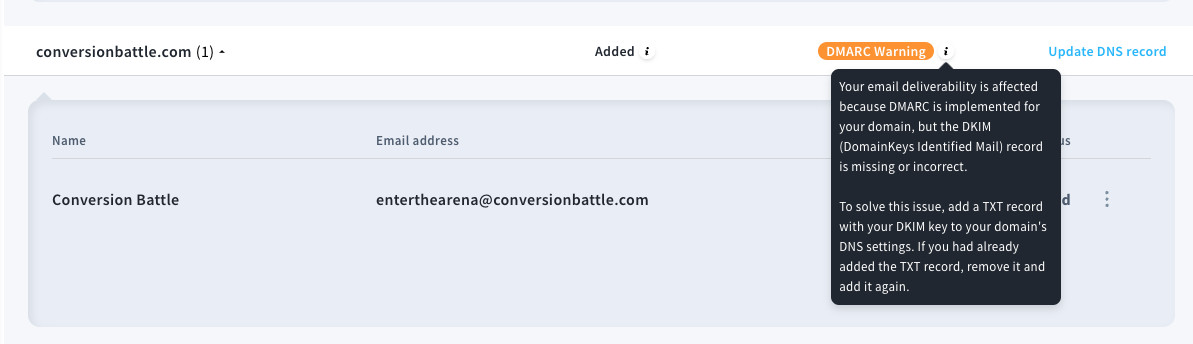
GetResponse dashboard shows you tips on how to set up your domain for proper email campaign delivery
3. DMARC (Domain-based Message Authentication, Reporting & Conformance)
DMARC builds on SPF and DKIM. It does this by adding a policy to the DNS records of a domain. This policy specifies what action to take when an email fails SPF or DKIM checks—could be quarantining the email, rejecting it, or simply monitoring why it failed.
• Validator Tools
DMARC validator tools include PowerDMARC Checker Tool, DMARC-Validator.com, EasyDMARC DMARC Record Checker, DMARC-checker.org, and MXToolbox DMARC Check Tool.
The key parameters these DMARC tools validate include:
- SPF Alignment: Ensures the domain in the "Return-Path" header matches the domain in the "From" address or aligns with it.
- DKIM Alignment: Verifies the domain in the DKIM signature aligns with the domain in the "From" address.
- Domain: Confirms that the necessary DNS records (DMARC, DKIM, SPF) are published and accessible
Here’s an example of a DMARC record:
v=DMARC1; p=reject; rua=mailto:[email protected]; adkim=s; aspf=s;
- v=DMARC1: Indicates there is a DMARC policy
- p=reject: Specifies that emails that fail SPF or DKIM checks should be rejected. p=quarantine indicates that servers should “quarantine” emails that fail, while p=none means even emails that fail can go through.
- rua=mailto:[email protected]: The email address that will receive the DMARC report. The report contains valuable insights that can help administrators adjust their DMARC policies.
- adkim=s and aspf=s: Indicates the DKIM and SPF checks are set to “strict”. You can also set them to “relaxed” by changing the s to r
DMARC relies on the proper SPF and DKIM authentication, so any issues with these protocols will lead you to fail the DMARC check.
4. BIMI (Brand Indicators for Message Identification)
BIMI is an email authentication standard that enhances email security and user experience by allowing brands to display their logo alongside their authenticated emails in recipients' inboxes.
When an email passes DMARC authentication checks, supporting email clients like Gmail, Apple Mail, and Yahoo display the brand's logo in the inbox. Notice the difference between emails with a BIMI and those without.
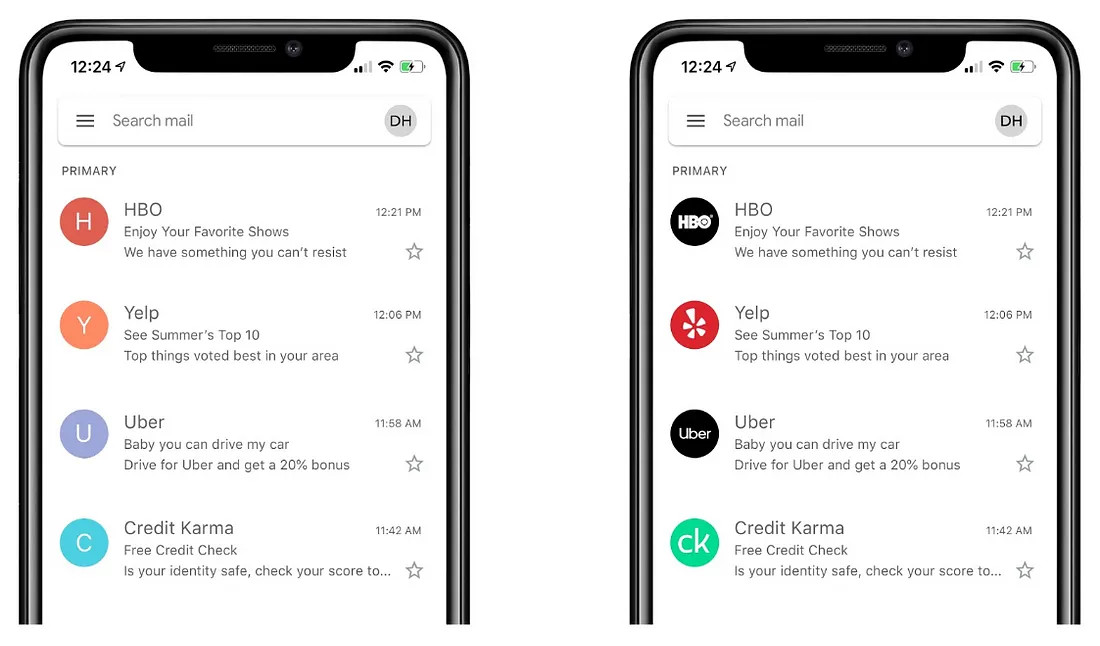
The visual indicator helps recipients recognize your brand in their inbox and also reassures you are the legitimate sender.
These emails will of course have higher open rates and conversion rates compared to unauthenticated emails. Complement these with landing pages that are optimized with tools such as Nostra and Intellimize for the best results.
• Validator Tools
The key tools you can use to validate BIMI records include EasyDMARC BIMI Record Checker, SimpleDMARC’s BIMI Checker, GoDMARC BIMI Record Lookup Tool, Valimail BIMI Validator, and VeriMarkCert BIMI Checker.
These BIMI validator tools typically check the following parameters:
- Presence of BIMI Record: They check for a well-configured BIMI DNS record for the domains.
- Logo Validity: Verify that the logo file meets the required specifications and is accessible via the URL specified in the BIMI record.
Here’s a great example of a BIMI record:
v=BIMI1; l=https://your-domain.example/path/to/logo.svg; a=https://your-domain.example/path/to/vmc.pem
- v=BIMI1: Specifies the BIMI version.
- l=https://your-domain.example/path/to/logo.svg: Indicates the URL of your logo in SVG format.
- a=https://your-domain.example/path/to/vmc.pem: Points to the URL of your Verified Mark Certificate (VMC), which proves ownership of the logo
For BIMI to function, the domain must have strong DMARC authentication policies set to either “quarantine” or “reject.” This means there’s never a situation where BIMI is the only layer of security.
Conclusion
Email authentication protocols like SPF, DKIM, DMARC, and BIMI work together to prevent unauthorized use of your domain and protect your brand’s sender reputation. This then helps improve email deliverability.
So, implement these email authentication protocols today.
Remember, email providers, like Yahoo and Gmail, have been enforcing email authentication requirements. Therefore, if you’re still wondering whether you need to familiarize yourself with these protocols and their validator tools, the answer is a resounding YES.






