Whenever you read anything on sending emails, it’s common to see abbreviations SPF, DMARC, and DKIM threw around casually. Don’t feel bad if you aren’t familiar with them since even techies may confuse these.
To make sure you know what those terms are as well as how to create SPF records and other records, take a look at this full guide describing the role and differences between these records. By the end of the post, you will have a solid understanding of why using them is important for your email marketing strategy.
Three Pillars of Email Authentication
Before we take a closer look at email records, let’s view the purpose of uniting them, namely authenticating email addresses quickly and efficiently.
Email authentication is a set of processes that helps prevent address forgery and phishing. It’s a crucial step towards protecting yourself from fraud.
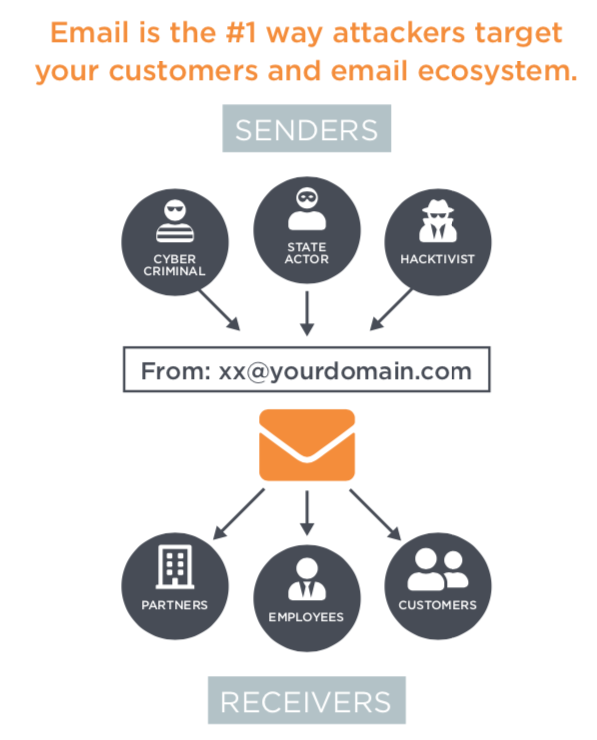
Source: Agari
If not for authentication tools, a fraudster could, for example, use the [email protected] address to trick taxpayers into paying a ton of money.
How does email authentication work?
The goal of email authentication is to allow address owners to have full control over who is sending emails on their behalf. Here’s a short overview of the main authentication processes.
- A domain owner creates a set of rules that determine that an email attached to the domain is legitimate.
- The software marketers use to launch their campaigns offers the infrastructure for ensuring email authentication.
- After receiving an email, a recipient server checks it against the rules a domain owner established.
- If an email is authenticated safely, a recipient will see it in the inbox. If the letter doesn’t meet one or several authentication criteria, the server will either flag a letter and show a recipient a warning or reject the email altogether.
Top Authentication Standards: SPF, DKIM, DMARC
By definition, SPF, DKIM, and DMARC are technologies used to determine that a sender is fully authorized to send an email using a chosen domain. Since, according to statistics, phishing makes up to 32% of all data breaches, email providers need to go the extra mile when authenticating user emails.
That’s why most email clients ask users for SPF, DKIM, and DMARC records before sending emails on the domain’s behalf.
Let’s t consider what each of these records is, and how you can fill it in to ensure email safety.
1. SPF
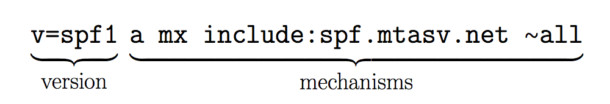
Source: Postmark
Sender Policy Framework (SPF is a TXT-based list of emails and IP addresses of senders who are authorized to send messages using the company’s domain name. If an email server detects an address that’s not on the record, it will flag the email and not deliver its messages.
Setting SPF up protects senders from spoofers - people who hijack the addresses of others and start spamming taking advantage of their domains.
SPF record structure
Although things are going to get a little techy here, understanding the anatomy of the Sender Policy Framework will help team managers set it up.
Generally, an SPF record looks the following way:
v=spf1 +a +mx +ip4:108.123.111.114 -all
Looks complicated? The truth is, once deciphered, the structure of SPF becomes manageable and straightforward.
Let’s break it down:
- v=spf1 stands for the version of your SPF record. Right now, spf1 is the standard version of the record so email clients would be asking for records that have a v=spf1 indicator.
- a is the name of the record where a sender stores the list of authorized senders.
- mx refers to the servers a sender uses to exchange emails with recipients. It’s a convenient way to list several email servers at once since you don’t have to name them individually.
- Ip4: [ipname] – the IP of an authorized sender. Although the sample SPF features only one address, you can add more (don’t forget to separate them with a comma).
- all is a process of matching a sender’s address against all the criteria listed in the record.
SFP Authentication-Results: Pass, Fail, Soft Fail, Neutral
When a mail server finishes the SPF authentication process, it shares feedback with the sender. There are four types of authentication results you can get:
-
- Pass: the sender is legitimate.
- Fail: the sender is not allowed to send emails using the domain.
- Soft Fail: emails that the senders share will be flagged.
- Neutral: the sender doesn't want to share data on the IP authorization.
How to Set Up SPF?
Now that you understand the anatomy and the output of the sender policy framework, let’s take a look at how to create SPF records.
Here’s a step-by-step guide to the SPF setup.
- Collect the list of authorized IP addresses.
- Create a list of domains these senders are allowed to use.
- Create an SPF record based on the structure explained above.
- Submit the record to the Domain Name System.
- Run tests to ensure the SPF record is active.
2. DKIM
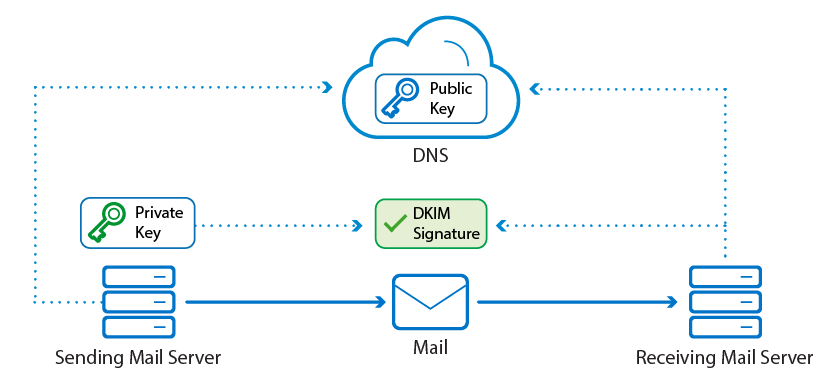
Source: Barracuda
DKIM (Domain Keys Identified Mail) adds an encrypted header to all the messages a legitimate sender sends to protect the address from spoofing. Although some email clients (like Gmail) generate a DKIM record for each address, it’s better for domain owners to create a unique key on their own.
The process of setting up DKIM consists of three steps:
- Generating a pair of keys using dedicated tools. The software you choose depends on your operating system. Windows users can consider PUTTYGen, whereas macOS adopters can use ssh-keygen instead.
- Adding the key to the DNS record in the TXT format. Depending on the hosting service provider, the process of DKIM integration might vary - here are the examples for GoDaddy and Amazon Route 53.
- Creating a signature using an SMTP server.
If you are wondering whether all the effort put into setting up DKIM is worth the effort, let’s examine the benefits of having an encrypted signature:
- Protection. It helps protect your email from spoofing and phishing. A hacker will not be able to take advantage of your address.
- Email deliverability. Email service providers are more likely to deliver your personal or commercial messages from a DKIM-certified address, as opposed to unauthorized senders.
- Sender reputation. Emails with no DKIM record are seen by ESPs as suspicious as they get a lower sender score.
3. DMARC
Other than being an important line of phishing defense, DMARC hugely impacts the deliverability of email marketing campaigns. Setting up the record helps senders keep their emails outside the most popular blacklist and improves sender reputation.
What is DMARC?
DMARC is the abbreviation for Domain-based Message Authentication, Reporting & Conformance. Despite its fancy name, in reality, DMARC is just a set of three DNS records that flag and reject fraudulent emails.
Here’s how DMARC works:
- It checks the DKIM record of a domain owner and determines whether an address in question matches it.
- It validates the SPF record to make sure that a server the email is coming from is authorized.
- If both checks are successful, DMARC delivers the email to the sender.
A DMARC record is written using tags. The three most common ones are rua, v, and p. Let’s take a closer look at each of these:
- v is the “version” tag that indicates the version of the record the provider is using.
- p is the “policy” tag that determines which actions a domain owner wants to take if a sender doesn’t pass the check. It can either be set to: none (no preventive actions, quarantine (flags email and delivers it to spam), reject (doesn’t deliver the message).
- rua determines where DMARC reports are sent. Next to the tag, a sender can specify an email of a person in charge of tracking sent emails.
There are other DMARC tags that you can include in the record. However, they are secondary.
Conclusion
Email authentication records are a powerful line of defense against spamming, spoofing, and phishing. There are three standard records you need to enable to make sure ESPs aren’t considering the campaigns suspicious and protect the company’s domain name - SPF, DKIM, and DMARC.
Since all three are highly important, there’s no need to prioritize one over the other. Get in touch with your tech team to set up these records, run some tests, and feel free to launch a campaign. After authenticating your address, you’ll be capable of sending and receiving emails securely and efficiently.



![Email Accessibility Guide [2025]](https://ik.imagekit.io/debounce/wp-content/uploads/2022/07/email-accessibility-guide-2-300x139.png)
![Mail Merge Explained: Definition, Uses, Tutorial [2025]](https://ik.imagekit.io/debounce/wp-content/uploads/2024/06/mail-merge-explained-300x139.png)

